windows降权记录
转载请注明出处:https://youngrichog.github.io/
降权模式:
- SYSTEM -> 普通用户
- 用户A -> 用户B
一种是SYSTEM降权至普通用户,另外一种是用户A使用用户B身份
降权方式:
- 令牌窃取
- 模拟用户
- 切会话
- 进程迁移/进程注入
测试环境
Ubuntu - 攻击者
Windows10 x64 - 受害者
Widnows7 x64 - 受害者
令牌窃取
典型工具:incognito
下载地址:https://labs.mwrinfosecurity.com/tools/incognito/
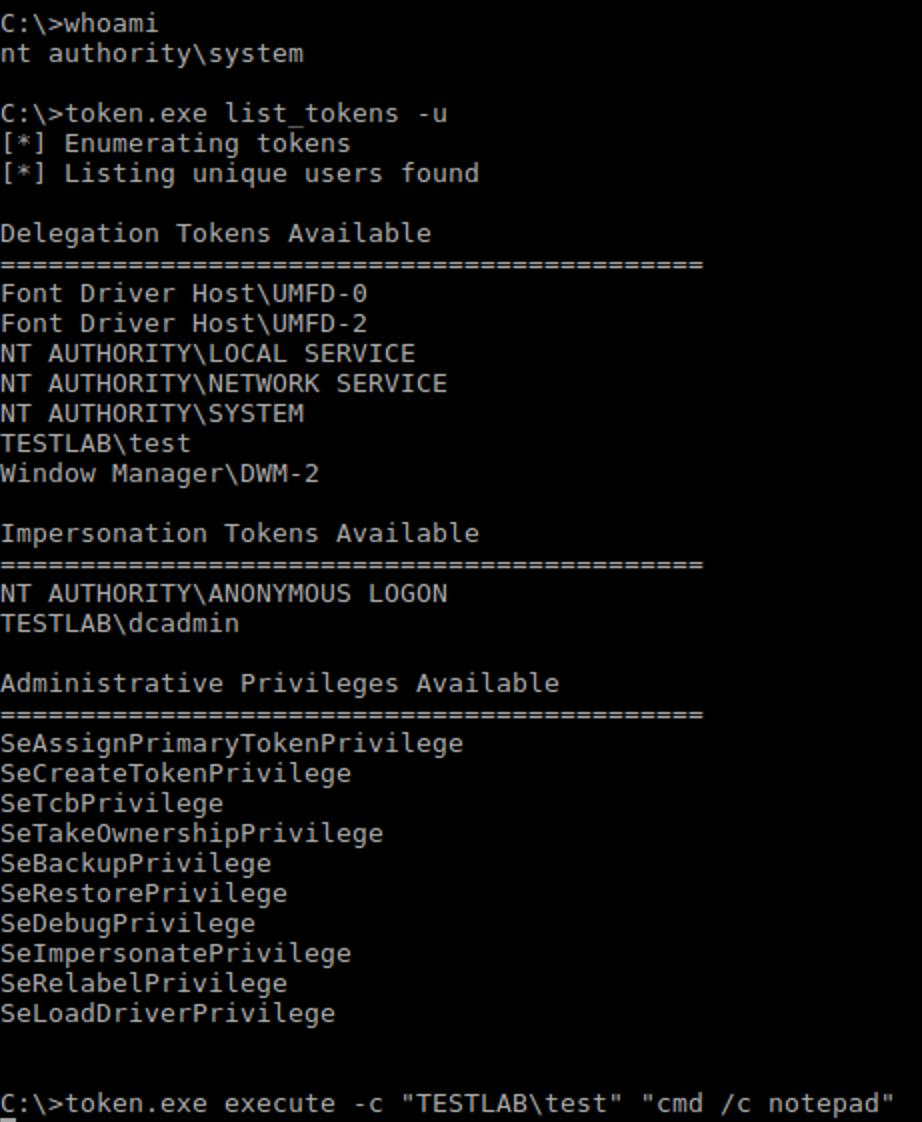
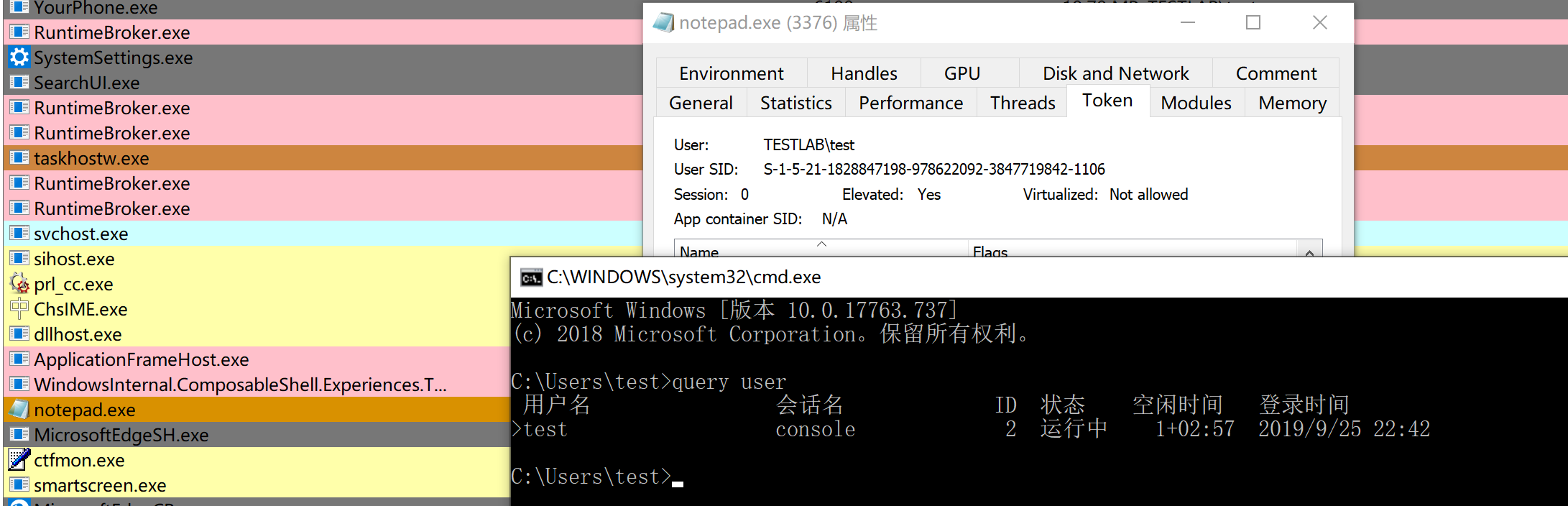
结果:成功
模拟用户
典型工具:RunAs
下载地址:https://www.verydoc.com/exeshell.html#CmdAsUser_Command_Line_Tool
还有其他的,如:https://github.com/JetBrains/runAs,这里有一个点就是,利用系统自带的runas目前没有找到合适解决自动输入密码的方式。
1 | JetBrains runAS: |
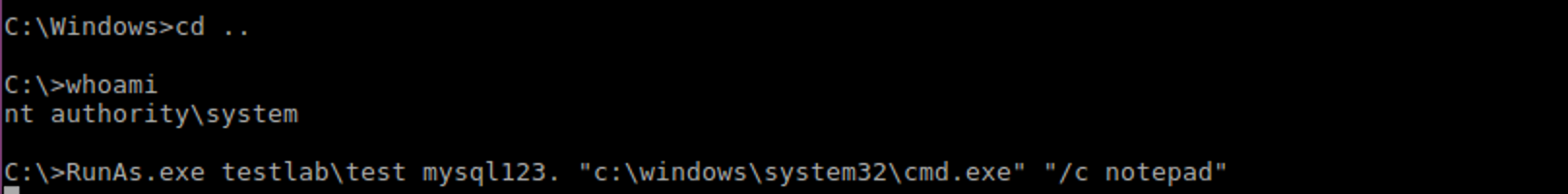
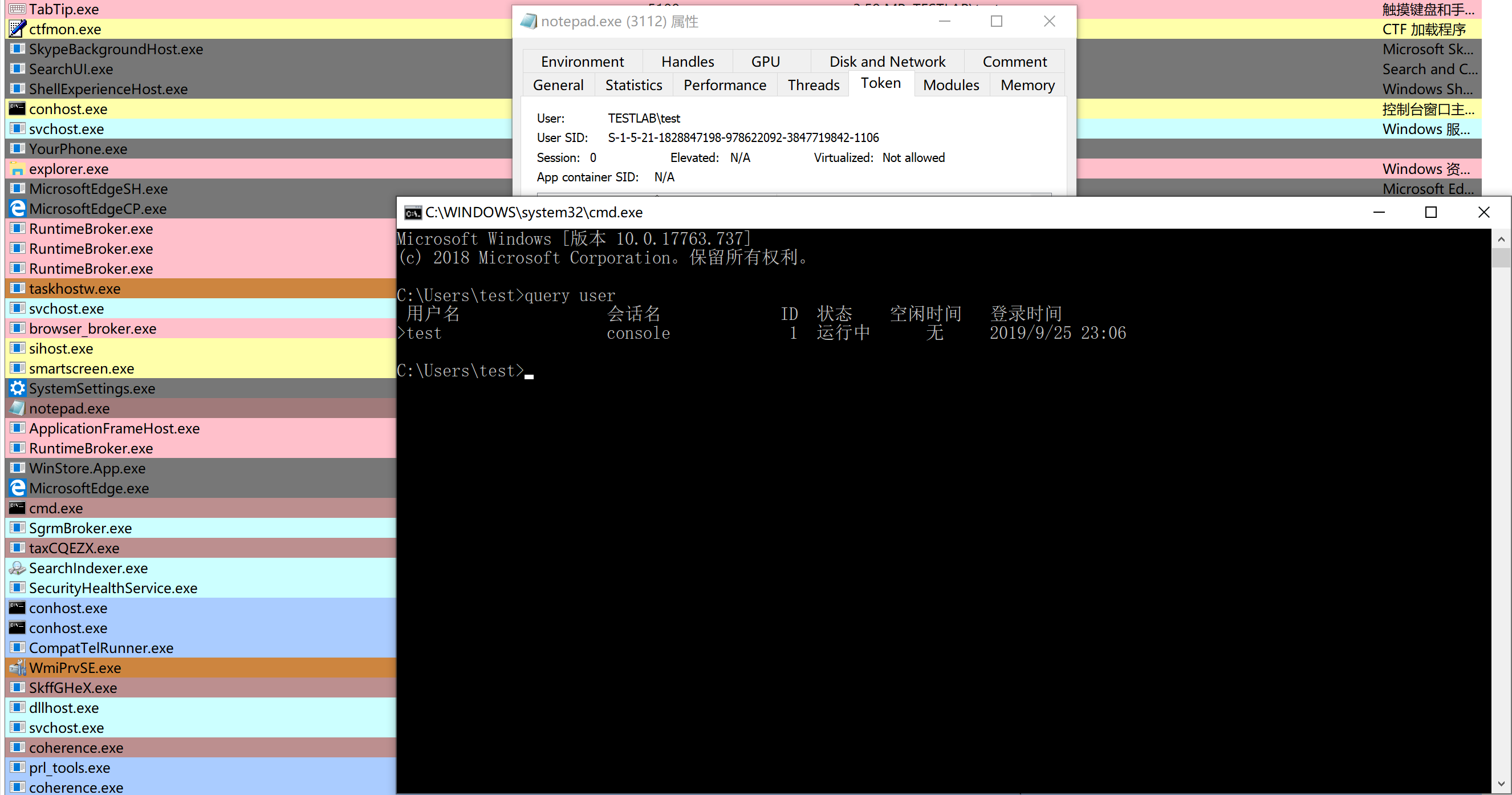
结果:成功
切会话
从上面令牌窃取和模拟用户看到,我们都无法和真正的用户在同一个Session里,那么就会存在一些问题,例如:键盘记录、屏幕截图、屏幕监控等,这些都是没有办法实现的。当需要这样场景的时候就需要进行切会话,切到同Session下就可以完成上述行为。
进程迁移/进程注入
- Get the PID the user wants to migrate into. This is the target process.
- Check the architecture of the target process whether it is 32 bit or 64 bit. It is important for memory alignment.
- Check if the meterpreter process has the SeDebugPrivilege. This is used to get a handle to the target process.
- Get the actual payload from the handler that is going to be injected into the target process. Calculate its length as well.
- Call the OpenProcess() API to gain access to the virtual memory of the target process.
- Call the VirtualAllocEx() API to allocate an RWX (Read, Write, Execute) memory in the target process
- Call the WriteProcessMemory() API to write the payload in the target memory virtual memory space.
- Call the CreateRemoteThread() API to execute the newly created memory stub having the injected payload in a new thread.
- Shutdown the previous thread having the initial meterpreter running in the old process.
上面这样貌似是一个标准的写法
思考🤔
目前脑子里只有这些东西
Respect
https://jlajara.gitlab.io/posts/2018/11/26/process-migration.html